

Blockchain is an emerging technology that is quite popular nowadays due to the popularity of cryptocurrency. Apart from blockchain being used in cryptocurrency, it is also marketed as a cure for a lot of things including cybersecurity. Blockchain is considered to be a nearly impenetrable technology as by design, blockchain is resistant to modification of the data. The blockchain contains a list of records or blocks which are linked using cryptography. Each of those individual records/blocks contains information and data that are combined together and verified. Information such as a cryptographic hash function of the previous block, timestamp, and transaction details are permanently recorded in a distributed ledger. The ledger is decentralized in nature, all transactions are done across a peer-to-peer network. Blockchain technology is designed in such a way that there is no central authority or storage location. Every user on the network plays a part in storing some or all of the blockchain. Everyone is responsible for verifying the data that is stored and/or shared to make sure false data cannot be added and existing data cannot be removed.
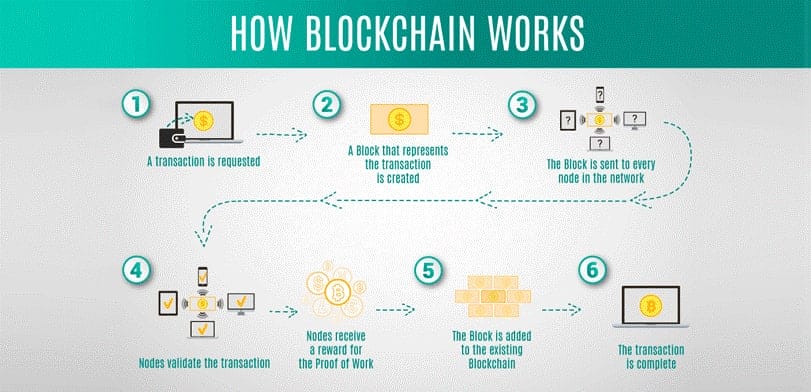
Blockchain technology has been around for more than a decade. It was invented by a person using the name Satoshi Nakamoto in 2008 to serve as the public transaction ledger of the cryptocurrency bitcoin. However, as technology has gradually spread worldwide, people have begun using it in a variety of ways in numerous industries, including as a means to increase cybersecurity. Blockchain is a chain of records that leads to the formation of a distributed network that can have millions of users all over the world. Every user can add information to the blockchain and all data in the blockchain is secured through cryptography. Every other member of the network is responsible for verifying that the data being added to the blockchain is real. This is done using a system of three keys private, public, and the receiver’s key that allow members to check the veracity of the data while also confirming whom it comes from. The verified data then form a block and will be added to the chain of data. In order to make updates to a particular piece of data, the owner of that data must add a new block on top of the previous block, creating a very specific chain of code.
The network being accessed by an unauthorized person can lead to data being either stolen or damaged. Hence, it becomes essential for an individual or organization to determine the invasion. The mode of collecting and preserving evidence has a significant role to play in ensuring that the evidence is accountable in the courtroom during various situations such as lawsuits or criminal complaints.
Identifying the attack/breach and generating the required documents about the causes of cyber-attack or cyber fraud can be accountable through the use of blockchain technology. Truth-based evidence is always important in any cybercrime investigation. Digital evidence moves down the hierarchy through the chain of custody in the different levels of transactions in any investigation process. Blockchain technology can provide a clear and exhaustive view of the transactions that have taken place concerning the evidence, right from the time the evidence originated from the source [2].
There are many reported cases of missing police evidence and several of them go unaccounted for giving an easy way out for criminals, such types of things can also be prevented using blockchain technology. It can enable appropriate authorization to those who are permitted to enter the evidence room, whether electronic, magnetic, or by using private keys. The scientific approach in digital forensics flow through the search authorities, the chain of custody of evidence, imaging and hashing function, validation of data using appropriate tools, report-ability, and repetition of presentation. The entire process can be made data-centric using blockchain technology.
The hash validation with the blockchain and the timestamp will prevent repeatability and contamination of information. Keeping a clear and unique track of who accessed what and when will help to avoid the contamination of evidence and information. The blockchain technology-based application can be used to ensure proper operating practice when it comes to evidence management practices. Necessary questions like How the core data is stored, how it is communicated, who is the person responsible for handling the data, and the factors that contribute to the physical security of the data can all be streamlined efficiently. Ideas such as working with the duplicate copy and not with the original can be validated using the hash. The Hash function will take the data and will generate a fixed-sized bit sequence in the output. Thus, creating a digital fingerprint of the input data.
The number of people joining the world wide web and technology is continuously growing and developing at a very fast rate, more data gets produced and more hackers will attempt to steal or corrupt that data. The technology behind blockchain is flexible and unbelievably helpful for the future of the Internet, permitting users to better secure their data. Innovative uses for blockchain technology are already becoming a part of other fields beyond cryptocurrencies and can be especially useful to boost cybersecurity. Blockchain implementation will facilitate in forestall a lot of threats and attacks in a very system and might forestall the information from being taken or destroyed. A number of the items that blockchain will facilitate are: –
I. Preventing Fraud and Theft of data: – Blockchain technology provides one of the best securities to protect data from hackers by preventing potential fraud and decreasing the chance of data being stolen or compromised. In order to destroy or modify blockchain, a hacker would have to destroy the data stored on every user’s computer in the global network. This could be millions of computers, with each one storing a copy of some or all the data. Bigger blockchain networks with more users have an infinitely lower risk of getting attacked by hackers because of the complexity required to penetrate such a network.
II. Preventing Distributed Denial of Service (DDOS) Attacks: – Hackers can use several techniques to launch an attack, most common is sending a large number of requests/packets to the system until the system becomes unable to process these requests/packets and leading to the failure/crash of the system. DDoS attacks have been happening at an increased frequency recently, affecting bigger companies like Twitter, Spotify, SoundCloud, and more. The current difficulty in preventing DDoS attacks comes from the existing Domain Name System (DNS). The fact that it is only partially decentralized means that it is still vulnerable to hackers because they are able to target the centralized part of DNS and continue crashing one website after another. Implementing blockchain technology would fully decentralize DNS, distributing the contents to a large number of nodes and making it nearly impossible for hackers to attack. Domain editing rights would only be granted to those who need them (domain owners) and no other user could make changes, significantly reducing the risk of data being accessed or changed by unauthorized parties.
III. Decentralized Storage Solutions: –
Data is becoming more valuable than gold and oil. Every business and individuals accumulate tones of sensitive data about themselves or customers. Unfortunately, this data is also quite attractive to hackers. And one of the most convenient things you do for cybercriminals is to store all of it in one place. The business mainly is still using centralized storage when it comes to data. Blockchain-based storage solutions are slowly gaining popularity. An example of this can be Apollo data cloud which is developed by the Apollo Currency team allows users to archive data on the blockchain and grant permission for access to third parties. The cryptographic access key can be revoked at any time, further reducing the risk of a breach. Thanks to the decentralized nature of blockchain technology, hackers no longer have a single point of entry, nor can they access entire repositories of data in the event that they do get in.