Governance, Risk, and Compliance (GRC) plays a pivotal role in organizational success by providing a structured and integrated approach to managing an organization's overall performance, addressing risks, and adhering to
Governance, Risk, and Compliance (GRC) plays a pivotal role in organizational success by providing a structured and integrated approach to managing an organization's overall performance, addressing risks, and adhering to regulatory requirements.
An effective GRC approach not only ensures that organizations operate ethically and responsibly but also supports their overall success by enhancing decision-making, managing risks, maintaining compliance, and fostering stakeholder trust.
The integrated GRC approach formed by the key components, helps organizations operate ethically and responsibly while managing risks effectively and efficiently. By addressing governance, risk, and compliance holistically, organizations can enhance their performance, build trust, and ensure long-term success.
The key components of Governance, Risk, and Compliance (GRC) are:
GRC contributes to organizational success in several ways:
COMPASS is a niche light-weight Platform which can enhance your Internal Audit process and user experience.
In today's complex business landscape, integrating Governance, Risk, and Compliance (GRC) strategies into organizational practices is no longer optional but imperative. By embracing GRC, organizations can make informed decisions, effectively manage risks, maintain a strong compliance posture, and foster stakeholder trust. A well-implemented GRC approach leads to improved efficiency, enhanced performance, and, ultimately, long-term success. It is essential for organizations to recognize the significance of GRC, align their GRC strategies with business objectives, and continuously evolve their practices to adapt to the ever-changing business environment.
Compliance with government laws, regulations, and rules is essential for all organizations. A regulatory requirement is a directive imposed by a government entity on an organization. Numerous federal and state laws apply universally to organizations, dictating how they conduct their operations, manage employees, and engage with customers, among other aspects. Ensuring regulatory compliance is vital for any business, offering financial benefits by preventing fines and identifying potential vulnerabilities within the company.
Regulatory compliance involves adhering to government or industry laws and regulations to ensure ethical business practices. It protects organizations from penalties, safeguards reputation, and promotes public trust. Compliance includes understanding regulations, implementing policies, and monitoring adherence to maintain fair competition and consumer protection.
Regulatory bodies are organizations that create and enforce rules for a particular industry or sector. Their goal is to ensure businesses operate ethically and legally. Regulatory bodies are often empowered by legislation and have the authority to set standards, conduct inspections, enforce compliance, and impose penalties for violations. They play a crucial role in consumer protection, helping to ensure products and services are safe, effective, and high quality.
Here is a list of regulatory bodies from various sectors:
These regulatory bodies oversee and enforce regulations to ensure compliance and maintain standards in their respective sectors.
Certin, or the Indian Computer Emergency Response Team (CERT-In), is a government agency within the Ministry of Electronics and Information Technology of India. It is the primary agency responsible for dealing with cyber security incidents in the country, and it works to strengthen the cyber security defense of the Indian Internet domain. CERT-In's role is to respond to cyber security incidents, provide guidance and support to organizations and individuals affected by cyber attacks, and help prevent future attacks through proactive measures such as vulnerability assessments and threat intelligence sharing. It also collaborates with international CERTs and other government agencies to exchange information and coordinate responses to cyber security incidents that cross national boundaries.
Streamlining Compliance: How COMPASS Can Help Organizations Navigate Regulations
COMPASS by CyRAACS, a niche, lightweight GRC product helps organizations address their compliance needs smarter, faster, and easier by Automating Information Security Compliances & Privacy Laws.
COMPASS can help organizations comply with regulations from Regulatory Bodies like RBI, SEBI, and IRDAI in several ways:
These features can help organizations stay compliant with RBI, SEBI, and IRDAI regulations, reducing the risk of non-compliance and avoiding potential penalties.
In today's complex business environment, regulatory requirements are essential for ensuring legal compliance, protecting consumers and the public, promoting fair competition, and maintaining public trust in businesses. Compliance with regulations is not only a legal obligation but also a strategic imperative that can bring numerous benefits, including reduced risk, improved reputation, and increased competitive advantage. By adopting a proactive and holistic approach to regulatory compliance, organizations can build a strong foundation for long-term success, create value for all stakeholders, and play a positive role in society.
In today's dynamic business landscape, organizations face an ever-increasing array of challenges, from regulatory compliance and cybersecurity threats to operational risks and data privacy concerns. To navigate these treacherous waters, companies must implement a holistic approach to governance, risk management, and compliance (GRC). This journey toward achieving effective GRC can be likened to setting sail on a sea of possibilities, with numerous islands of success to discover. But how do you embark on this voyage, and what can you expect to encounter along the way? Let's dive in and explore the intricacies of getting started with your GRC journey.
To begin our GRC journey, it's vital to understand what GRC entails. GRC is a structured approach that aligns an organization's objectives, policies, and procedures with the various risks and compliance requirements it faces. This alignment is crucial for maintaining the organization's integrity and resilience in an ever-changing business environment.
Governance: This involves defining the rules, roles, and responsibilities within an organization. Governance sets the direction and tone for the entire GRC strategy and ensures that objectives are clear and well-communicated.
Risk Management: Risk management is all about identifying, assessing, and mitigating risks that could impact the organization's ability to achieve its goals. It is the heart of GRC, helping to protect the organization from potential pitfalls.
Compliance: Compliance encompasses adherence to laws, regulations, and internal policies. Ensuring compliance is not only a legal obligation but also essential for maintaining the organization's reputation and customer trust.
As we embark on our GRC journey, let's dive into a real-world example in the Healthcare Industry to guide us on our path and to introduce these concepts:
Imagine a healthcare provider with multiple facilities nationwide. This organization is entrusted with the sensitive healthcare data of countless patients, and compliance with regulations like HIPAA (Health Insurance Portability and Accountability Act) is paramount.
Governance: To start their GRC journey, the healthcare provider established clear governance. They defined the roles and responsibilities within the organization to ensure that objectives, like safeguarding patient data, were well-communicated.
Risk Management: The organization conducted a comprehensive risk assessment to identify vulnerabilities in its data storage and transmission processes. This helped them in assessing the risks involved in protecting patient information.
Compliance: They implemented a robust compliance program, conducting regular HIPAA audits and training their staff to ensure compliance with the law.
This real-world example highlights the importance of understanding the GRC framework. Defining objectives, roles, and responsibilities (governance), assessing vulnerabilities (risk management), and ensuring compliance with healthcare regulations (compliance) were the critical first steps of their GRC journey.
Managing Governance, Risk, and Compliance (GRC) within an organization involves structured processes and integration of people, technology, and policies. Here's a brief overview of how GRC is managed:
By aligning these elements, organizations can effectively navigate risks and regulations while achieving their objectives and long-term success.
COMPASS, a specialized lightweight platform, enhances your Internal Audit and external audit processes and user experience. Some of the benefits of using COMPASS include:
In conclusion, embarking on a GRC journey is crucial for organizations to navigate the complex seas of governance, risk management, and compliance. This holistic approach requires a strong foundation in governance, proactive risk management, and adherence to compliance standards. Real-world examples demonstrate the effectiveness of GRC initiatives, with healthcare providers and financial institutions showcasing the importance of understanding the GRC framework. As you set sail on your GRC journey, remember that it's an ongoing process with no fixed destination, but the rewards in terms of resilience and success are well worth the effort.
Information security is a critical concern for organizations in the digital age, as the proliferation of data and technology brings new vulnerabilities and threats. To safeguard sensitive information, organizations must conduct information security risk assessments. This comprehensive guide will walk you through the key steps and best practices involved in conducting an effective information security risk assessment, ensuring the confidentiality, integrity, and availability of data.
A methodical procedure known as risk assessment finds, assesses, and eliminates possible dangers and threats to the information assets of a company. In order to help organisations make wise decisions and deploy resources efficiently, it entails evaluating the possibility and impact of security incidents and vulnerabilities. The following are the necessary actions and recommended procedures for carrying out risk assessments:
It's critical to establish the parameters and context before beginning a risk assessment, this phase involves the following tasks:
The second step involves identifying the information assets and understanding how they flow through the organization:
During this stage, you determine possible dangers and weaknesses that can jeopardise your data assets:
Evaluation of the possibility and consequences of threats and vulnerabilities is a component of risk assessment.
Once risks have been identified, it is critical to rank them according to importance:
Developing solutions to manage risks is essential after you've identified and prioritised them:
A risk assessment needs to be monitored continuously and reviewed on a regular basis:
Organisations must proactively detect, assess, and mitigate possible threats to their information assets, which makes information security risk assessment an essential practise in today's digital world. Ensuring the security, integrity, and availability of data requires following a methodical approach, involving important parties, and abiding by best practises. Organisations across a range of industries can preserve their stakeholders' trust, abide by legal obligations, and protect sensitive data by carrying out efficient information security risk assessments.
COMPASS, a specialized lightweight platform, enhances your Internal Audit and external audit processes and user experience. Some of the benefits of using COMPASS include:
Risk Assessment is a methodical process helps to identify, assess, and mitigate potential threats to your information assets, ensuring their confidentiality, integrity, and availability.
Key benefits of conducting an IS risk assessment include:

1. Purchasing ISO 27001 document – Your organization must purchase the ISO 27001 document and understand how to implement a structed ISMS for your organization. This will help your organization to understand why the controls are necessary and how they can be implemented to mitigate risks.
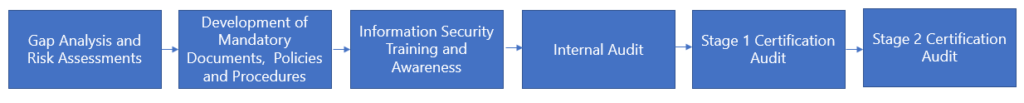
2. Gap Analysis - Before ISO 27001 certification, a gap analysis, is an essential process to find the "gaps" or discrepancies between your organization's current Information Security Management System (ISMS) and the ISO 27001 standard's standards. Gaps in implementation of information security controls in-line with ISO 27001 controls will be identified in this phase.
3. Risk Assessment - The information security management process requires a critical stage that involves doing a risk assessment against the controls in ISO 27001. Through this approach, your organization can assess the risks related to its information assets and define the security measures that are required to reduce those risks. The security measures to be defined and implemented must be selected according to the controls in ISO 27001 document against which the risks were identified. Choosing controls that aid in reducing or managing the risks that have been identified is the aim.
4. Establishing Governance and Responsibilities - Information Security Management System (ISMS) requires establishing governance and responsibilities in accordance with ISO 27001 standards. Information security governance can be established and implemented using the framework offered by ISO 27001. Top management of your organization, including the CEO and board of directors, should exhibit a resolute dedication to information security. They should endorse the implementation of ISO 27001 and provide resources to ensure its success. An Information Security Steering Committee must be formed to provide oversight and guidance for the ISMS. This committee should include key stakeholders from various departments and ensure that information security aligns with business objectives. The roles and responsibilities of individuals and teams involved in information security must be defined. This should include responsibilities for the CISO, IT staff, data owners, and other relevant parties.
5. Development of mandatory documents, policies, and procedures - Creating information security policies and procedures and other mandatory documents are essential steps in becoming certified to ISO 27001. These documents are essential to the creation of an extensive Information Security Management System (ISMS) that complies with ISO 27001 requirements and protects sensitive data within your organization. The foundation of your organization's security commitment is defined by its information security policies, which are supported by procedures that provide useful guidance for implementing these policies. The Information Security Policy, Risk Assessment and Treatment Methodology, Statement of Applicability (SoA) outlining specific security controls, records of internal audits and management reviews, and documented proof of employee training and awareness programs are among the mandatory documents needed for ISO 27001 certification. When taken as a whole, these documents show a dedication to information security, a methodical approach to risk management, and a thoroughly documented system for observing and enhancing security procedures—all crucial components for ISO 27001 compliance.
6. Conducting Internal Audit – The next essential step before obtaining ISO 27001 certification is carrying out a comprehensive internal audit. The purpose of this internal audit is to evaluate your organization's Information Security Management System (ISMS) in comparison to ISO 27001 requirements and standards. To find opportunities for improvement and compliance gaps, it functions as a critical examination of your organization's current information security policies, processes, and controls. During an internal audit, staff members are usually interviewed, paperwork is reviewed, and the efficacy of security measures is assessed.
7. Stage 1 Audit - The first phase in the ISO 27001 certification procedure is the Stage 1 audit. It entails evaluating the documentation, policies, and procedures of your organization's information security management system (ISMS) to determine whether they comply with ISO 27001 requirements. Finding any holes or inconsistencies in the ISMS, verifying the ISMS's scope, and assessing your organization's preparedness for the ensuing Stage 2 audit are the main goals of the Stage 1 audit.
Key Items to Keep in Mind Before Stage 1:
8. Stage 2 Audit - The second and more thorough stage of the ISO 27001 certification procedure is the Stage 2 audit. The primary objective of this audit is to assess how well your organization's Information Security Management System (ISMS) is really implemented and operating in compliance with ISO 27001 requirements. Your organization's overall ISMS procedures and security measures will be evaluated. In-depth examination of the organization's risk assessment and management, evidence collection, and stakeholder and employee interviews are all part of this phase. ISO 27001 accreditation, which signifies the organization's dedication to information security and efficient risk management, is obtained with the successful completion of the Stage 2 audit.
COMPASS, a specialized lightweight platform, enhances your Internal Audit and external audit processes and user experience. Some of the benefits of using COMPASS include:
Obtaining ISO 27001 certification is a significant accomplishment that signifies an organization's commitment to information security and best practices. Achieving this certification requires a structured approach and dedicated effort, but the benefits are numerous:
In the age of digitalization, where personal data has become a valuable commodity, the need for robust data protection laws has become increasingly crucial. Recognizing this need, India has enacted the Digital Personal Data Protection Act, 2023 (DPDPA), marking a significant milestone in the country's data privacy landscape. This comprehensive law aims to empower individuals with control over their personal data and establish a framework for responsible data processing practices.
On August 9, 2023, the Indian Parliament rocked the data world by introducing the Digital Personal Data Protection Act (DPDP Act). India's very first data privacy superstar, this act hands you the reins to your personal data, while giving businesses a crash course in data manners.
The DPDPA applies to all organizations that process the personal data of individuals located in India, regardless of the organization's location. This broad applicability ensures that Indian citizens are protected, even when foreign companies process their data. The Act also applies to organizations that offer goods or services to individuals in India, even if the organization is not physically present in the country.
Here are key points we should know before jumping deep down in DPDPA
A data principal is an individual to whom personal data relates. This means that the individual is the person whose personal data is collected, used, or disclosed. Data principals have certain rights under data protection laws, such as the right to access, rectify, erase, and restrict the processing of their personal data. They also have the right to object to the processing of their personal data and to receive their personal data in a structured, commonly used, and machine-readable format.
A data fiduciary is an organization that determines the purposes and means of processing personal data. This means that the data fiduciary is the entity that decides how and why personal data will be collected, used, or disclosed. Data fiduciaries have certain obligations under data protection laws, such as the obligation to collect only the personal data that is necessary for the specified purpose, to process personal data fairly and accurately, to implement appropriate technical and organizational measures to protect personal data and to be able to demonstrate compliance with the data protection law.
A data subject is an individual to whom personal data relates. This is the same as a data principal. The terms "data principal" and "data subject" are often used interchangeably. However, the term "data principal" is more commonly used in the context of the DPDPA.
The DPDPA outlines several key provisions that govern the collection, use, and disclosure of personal data. These provisions are designed to protect individuals' privacy and ensure that their data is handled responsibly.
Data Principals' Rights:
The DPDPA grants individuals, known as "data principals," several rights regarding their personal data. These rights include:
2. Data Fiduciary Obligations:
Organizations that process personal data are designated as "data fiduciaries" under the DPDPA. Data fiduciaries have several obligations, including:
3. Data Processing Frameworks:
The DPDPA establishes different frameworks for the processing of personal data based on the sensitivity of the data and the purpose of processing. These frameworks include:
4. Cross-border Data Transfers:
The DPDPA restricts the transfer of personal data outside of India unless the recipient country has an adequate level of data protection.
5. Enforcement and Penalties:
The DPDPA establishes a Data Protection Authority (DPA) to oversee the implementation of the law. The DPA has the power to investigate complaints, issue penalties, and take other enforcement actions. If a data breach occurs, the data fiduciary is required to notify the Data Protection Authority (DPA) within 72 hours of becoming aware of the breach. The DPA may then investigate the breach and take enforcement action, such as imposing a penalty.
The penalty for a data breach under the DPDP Act can be up to 250 crore INR ($30 million). The amount of the penalty will depend on the severity of the breach and the harm caused to the data subjects. The DPDP Act also provides for criminal penalties for certain types of data breaches, such as those that involve the personal data of children. The maximum penalty for a criminal data breach is imprisonment for up to three years, or a fine of up to one crore INR ($125,000), or both.
COMPASS, a specialized lightweight platform, enhances your Internal Audit and external audit processes and user experience. Some of the benefits of using COMPASS include:
The DPDP Act is a significant step forward for data protection in India. It gives individuals more control over their personal data and sets out rules for how businesses can collect, use, and share personal data. However, the act is not without its challenges.
One challenge is the cost of compliance. Businesses will need to invest in new systems and processes to comply with the act. Another challenge is the lack of clarity in some of the provisions of the act. This could lead to disputes between businesses and individuals.
Despite these challenges, the DPDP Act is a positive step for India. It will help to protect the privacy of individuals and make it more difficult for businesses to misuse personal data. The act will also help to create a more level playing field for businesses and give them confidence to invest in India.
Here are some of the potential impacts of the DPDPA on India:
• The act could lead to increased investment in data protection by businesses.
• The act could help to create a more secure environment for personal data in India.
• The act could help to boost innovation in the data economy.
• The act could help to protect the privacy of individuals in India.
The DPDP Act is a new law, and it remains to be seen how it will be implemented and enforced. However, it is a positive step for India, and it has the potential to make a significant impact on the country.
The General Data Protection Regulation is a law that was enacted in 2018, it has transformed the way businesses worldwide handle and protect personal data. With stringent requirements for data privacy and security, GDPR compliance is essential for organizations that collect, process, or store personal data of individuals in the European Union (EU), also extends to data of citizens of European Union (EU) being stored in other countries.
In this comprehensive guide, we'll walk you through the key aspects of GDPR compliance and provide a roadmap for ensuring your organization adheres to these regulations.
GDPR is a comprehensive data protection regulation that aims to provide individuals in the EU greater control over their personal data. It addresses how personal data should be collected, processed, stored, and protected by organizations. GDPR applies to businesses and entities located within the EU, as well as those outside the EU that handle the data of EU residents.
The following domains/areas are protected under GDPR for data of the citizens of the EU:
GDPR is a law and is applicable to any organization that stores, processes and uses data of citizens in the EU. The following entities have to be compliant with GDPR:
GDPR does not apply to companies which are service providers based outside the EU or if the company provides services to customers outside the EU.
GDPR grants several rights to its Data subjects, some of them are as follows:
Achieving GDPR compliance involves a series of steps to ensure your organization adheres to its principles and respects the rights of data subjects.
Irrespective of the size of your organization, you can give GDPR compliance a shot by following the processes listed below:
It is essential that you know your data. Conduct audits to establish what information you have and who has access to it. Make sure you can legally justify all your data processing activities and you have a clean understanding of all the processes and can convey the same in a clear manner.
Data privacy and data security must be always the primary focus. This includes implementing appropriate technical and organizational measures to protect data. Technical measures include but is not limited to encryption. Organizational measures include limiting the amount of personal data that is collected and deleting data that no longer serves any purpose. Encrypt or anonymize data wherever possible. Create and enforce an internal security policy for your team members. Conduct a data protection assessment and have clear processes defined to carry it out. In the event of a data breach, make sure you have well defined procedures to keep all employees informed.
Appoint someone who would be responsible for GDPR compliance over your organization. Make sure you sign data processing agreements between your organization and any third-party vendors whose services you avail. If your organization is outside the EU, appoint a representative within one of the EU member states. Appoint a DPO.
Transparency with customers is essential, at any point of time they should be able to request and receive information that you have about them. They should also be able to update or delete their information as and when they want to. They should also be able to terminate the processing of their data by your company with ease. It is up to you company to protect the rights of customers.
Following this checklist might not have you compliant with GDPR entirely, but it significantly reduces your exposure to risk and regulatory penalties.
Non-compliance with GDPR can result in significant fines, which can be as high as €20 million or 4% of an organization's global annual turnover, whichever is higher. Additionally, reputational damage and potential legal action from data subjects are other consequences of failing to comply.
COMPASS, a specialized lightweight platform, enhances your Internal Audit and external audit processes and user experience. Some of the benefits of using COMPASS include:
GDPR compliance is not an option but a legal obligation for organizations handling personal data of EU residents. By following the steps outlined in this guide, organizations can establish a robust data protection framework that not only meets GDPR requirements but also fosters trust with customers and stakeholders. Compliance is an ongoing effort, and staying up to date with regulatory changes is essential to maintaining data privacy and security in the digital age.
In today’s ever-evolving cyber and risk landscape, information security has come to the forefront to combat the sophistication of cyberattacks and the constantly changing technology framework. Two widely recognized information security standards stand out in this arena: ISO 27001 and SOC 2.
Both ISO 27001 and SOC2 provide companies with strategic frameworks and standards to measure their security controls and systems against. While both aim to fortify an organization's information security posture, they differ in their approach and applicability. Let's unravel the intricate details of these standards and decipher which one suits your organization's unique needs.
ISO 27001 is an international standard that provides a framework for managing information security risks. It is a prescriptive standard, meaning that it outlines specific controls that organizations must implement to achieve certification. ISO 27001 is a comprehensive standard that covers a wide range of topics, including physical security, access control, data security, and incident management. The ISO standard is developed and regularly updated by the International Standards Organization.

Scope and Focus: ISO 27001 takes a holistic approach to information security. It's about understanding, managing, and mitigating risks associated with information assets, encompassing everything from data protection to physical security.
Applicability: ISO 27001 adheres to a globally recognized set of standards. Its flexibility allows organizations to adapt and implement controls that suit their specific needs while following a structured framework. Versatility is the name of the game with ISO 27001. From tech startups to healthcare institutions, any organization can harness its power to safeguard sensitive information.
Certification Process: ISO 27001 certification requires an annual audit conducted by an accredited certification body. ISO 27001 certification involves a rigorous process that culminates in a certificate validating an organization's compliance with the standard. Auditors from accredited certification bodies examine the entire system for its effectiveness in managing risks.
Requirements: ISO requires some mandatory documents for certification, the requirements are mentioned in the standard document and will be requested by the auditor during the audit. They are as listed below:
Reporting: The end result is a tangible ISO 27001 certificate, that will be given with an assessment report which will have the auditor’s findings based on the audit conducted.
Validity/Renewal: ISO 27001 certification is valid for three years, with surveillance audits conducted annually.
SOC 2 is a set of auditing procedures that are developed by the American Institute of Certified Public Accountants (AICPA). SOC 2 reports are designed to provide assurance to customers that an organization has implemented effective controls to protect their data. SOC 2 is a more flexible standard than ISO 27001, and it allows organizations to tailor their controls to their specific risks and needs. There are two types of SOC2 Audits, SOC Type 1 and SOC2 Type2:
SOC 2 Type 1 and SOC 2 Type 2 differ in the assessment and monitoring period of the internal controls. SOC 2 Type 1 evaluates the design of the security controls at a point in time, whereas SOC 2 Type 2 reviews the design and operating effectiveness of the controls over a period of 3-12 months.
While ISO 27001 is the jack-of-all-trades, SOC 2 Type 2 is specifically tailored to assess an organization's controls related to the five principles. This certification focuses on specific Trust Services Criteria—security, availability, processing integrity, confidentiality, and privacy.

Scope and Focus: SOC 2 Type 2 zeroes in on the trustworthiness and reliability of a service organization's systems. It ensures that customer data is secure, available, and confidential.
Framework and Standards: AICPA's Trust Services Criteria provides the foundation for SOC 2 Type 2. It's more industry-specific, tailor-made for service organizations dealing with sensitive customer information.
Applicability: This certification is the go-to for service providers, including cloud service companies, data centres, and software-as-a-service (SaaS) providers. It speaks directly to the concerns of customers entrusting their data to third parties.
Certification Process: The SOC 2 Type 2 certification process is unique, with independent CPA firms conducting audits. These audits evaluate controls over a defined period, usually six months or longer, ensuring they meet the Trust Services Criteria.
Reporting: The crown jewel of SOC 2 Type 2 is the comprehensive SOC 2 report. This report, issued by the CPA firm, outlines their findings, conclusions, and recommendations related to the controls in place.
Validity/Renewal: SOC 2 attestation reports are valid for one year, requiring annual re-attestation.
| Feature | ISO 27001 | SOC 2 |
| Type | Certification | Attestation |
| Definition | A standard that sets the requirements for an ISMS | Set of audit reports to evidence the level of conformity to a set of defined criteria (TSC) |
| Focus | Information security management system (ISMS) | Data security controls |
| Applicability | Designed to be used by any organization of any size or any industry | Organizations in the Service Industry across all industries |
| Scope | Comprehensive | Tailorable |
| Compliance | Certification issued by ISO Certification Body | Attestation by a Certified Public Accountant (CPA) |
| Audit | Annual (Surveillance) | Annual |
| Renewal | Every 3 years | Every year |
The ISO 27001 report is a detailed document that outlines the organization's ISMS. It includes information about the organization's information security policies, procedures, and controls. The report also includes the results of the audit, which will identify any areas where the organization needs to improve its information security.
The ISO 27001 report typically includes the following sections:
The SOC 2 report is a detailed document that outlines the organization's controls for one or more of the following Trust Services Criteria (TSC):
When it comes to ISO 27001 versus SOC 2 Type 2, the choice depends on your organization's nature and specific requirements. ISO 27001 is your passport to universal information security, applicable to diverse industries, while SOC 2 Type 2 is the trusted guardian of customer data for service providers.
The best report for your organization will depend on your specific needs and risks. If you are looking for a comprehensive report that outlines all of your organization's information security controls, then the ISO 27001 report may be a good option. If you are more concerned with providing assurance to your customers about your controls for a specific TSC, then the SOC 2 report may be a better choice.
COMPASS, a specialized lightweight platform, enhances your Internal Audit and external audit processes and user experience. Some of the benefits of using COMPASS include:
Whether you choose ISO 27001's structured framework or SOC 2's tailored approach, both standards offer valuable guidance in fortifying your organization's information security posture. Remember, the journey to information security excellence is an ongoing process, not a destination. By continuously evaluating, refining, and adapting your information security practices, you can safeguard your organization's sensitive data and maintain the trust of your customers.
Embarking on the journey of Governance, Risk Management, and Compliance (GRC) is a significant step for any organization in today's complex and highly regulated business environment. To thrive and ensure sustainable growth, businesses must proactively address governance issues, manage risks, and meet compliance requirements.
In this article, we will guide you through the crucial steps and considerations to get started with your GRC journey. Whether you're a large corporation or a small business, understanding the core principles and best practices of GRC is essential for not only surviving but excelling in a world where accountability and compliance are paramount.
GRC in Information Security refers to the integration of Governance, Risk Management, and Compliance (GRC) within the field of information security. While they are interconnected, they each serve a specific purpose for the Information Security Programs.
GRC helps organizations develop and maintain an effective Information Security program that protects sensitive data and systems, while also supporting business objectives and meeting compliance requirements.
A GRC journey involves multiple stakeholders with the organization, each playing different roles to ensure an effective and business aligned program. Some of the key stakeholders and their roles include:
COMPASS is a niche light-weight Platform which can enhance your Internal Audit process and user experience.
In the ever-evolving realm of cybersecurity, organizations face an unceasing challenge to secure their digital fortresses. A mid-sized financial services firm prides itself on its commitment to safeguarding customer data and financial assets. However, recent cyber threats have escalated, and the firm is keen to ensure that its cybersecurity defences remain resilient. In this scenario, a Gap Assessment becomes a crucial tool for the organization, allowing them to understand where they stand in the cybersecurity landscape, what gaps exist in their security measures, and how they can fortify their defences.
A Gap Assessment is a systematic and strategic process that evaluates an organization's current security practices, protocols, and technologies against industry standards, best practices, and compliance requirements. This assessment provides a holistic view of the organization's security posture and is essential in identifying vulnerabilities and security gaps.
In a rapidly changing world where technology evolves, regulations tighten, and threats become more sophisticated, organizations need a compass to navigate their way through the complex landscape of cybersecurity. Gap Assessments serve as that compass, providing the necessary guidance to understand where an organization stands, where it should be, and how to bridge the divide between the two. They are the essential tool that empowers businesses to proactively protect their assets, ensure compliance, and stay ahead of emerging threats. The benefits of an organization in performing a Gap Assessment are as follows:
Threat Readiness: Cyber threats evolve rapidly. To be prepared for emerging risks, organizations must identify vulnerabilities before malicious actors can exploit them. Gap Assessments enable organizations to stay ahead of the curve.
Compliance Adherence: Many industries, including finance, healthcare, and critical infrastructure, are subject to strict regulatory requirements. A Gap Assessment helps organizations ensure they meet these standards, avoiding hefty compliance penalties and maintaining trust with customers.
Data Protection: Data breaches are catastrophic to an organization's reputation and trust. For instance, an e-commerce business conducting a Gap Assessment may discover encryption protocol weaknesses, which, when addressed, protect customer data.
The Gap Assessment process is a structured and systematic approach that enables organizations to evaluate their current state and compare it to their desired state, whether in terms of cybersecurity, operational efficiency, or compliance. It can be done in the following way:
In the world of Gap Assessments, the right tools can make all the difference, enabling organizations to navigate the path from their current state to their desired state with precision and efficiency. Let's explore a range of powerful tools that empower organizations to conduct thorough Gap Assessments and take proactive steps toward achieving excellence in various aspects of their operations.
These tools empower organizations to not only identify gaps but also to take actionable steps in closing them, safeguarding their operations, and ensuring continuous improvement.
COMPASS, a specialized lightweight platform, enhances your Internal Audit and external audit processes and user experience. Some of the benefits of using COMPASS include:
In the high-stakes world of cybersecurity, Gap Assessments are indispensable for safeguarding digital assets and ensuring regulatory compliance. By employing a Gap Assessment, organizations can pinpoint and prioritize vulnerabilities, maintain regulatory adherence, and protect sensitive data. Tools like COMPASS by CyRAACS simplify and enhance this process, providing a clear roadmap to a safer and more resilient cybersecurity future.
Governance, Risk, and Compliance (GRC) plays a pivotal role in organizational success by providing a structured and integrated approach to managing an organization's overall performance, addressing risks, and adhering to
Compliance with government laws, regulations, and rules is essential for all organizations. A regulatory requirement is a directive imposed by a government entity on an organization.
In today's dynamic business landscape, organizations face an ever-increasing array of challenges, from regulatory compliance and cybersecurity threats to operational risks and data privacy concerns. To navigate
Information security is a critical concern for organizations in the digital age, as the proliferation of data and technology brings new vulnerabilities and threats. To safeguard sensitive information, organizations must conduct information security risk assessments. This comprehensive guide will walk you through the key steps and best practices involved in
Purchasing ISO 27001 document – Your organization must purchase the ISO 27001 document and understand how to implement a structed ISMS for your organization. This will help your organization to understand why the controls are necessary and how they can be implemented to mitigate risks.
In the age of digitalization, where personal data has become a valuable commodity, the need for robust data protection laws has become increasingly crucial. Recognizing this need, India has enacted the Digital Personal Data Protection Act, 2023 (DPDPA), marking a significant milestone in the country's data
The General Data Protection Regulation is a law that was enacted in 2018, it has transformed the way businesses worldwide handle and protect personal data. With stringent requirements for data privacy and security, GDPR compliance is essential for organizations that collect, process, or store
In today’s ever-evolving cyber and risk landscape, information security has come to the forefront to combat the sophistication of cyberattacks and the constantly changing technology framework. Two widely recognized information security standards stand out in this arena: ISO 27001
Embarking on the journey of Governance, Risk Management, and Compliance (GRC) is a significant step for any organization in today's complex and highly regulated business environment. To thrive and ensure sustainable growth, businesses must proactively address governance issues, manage risks, and meet compliance requirements. In this article, we will guide you through the crucial steps […]
In the ever-evolving realm of cybersecurity, organizations face an unceasing challenge to secure their digital fortresses. A mid-sized financial services firm prides itself on its commitment to safeguarding customer data and financial assets. However, recent cyber threats have escalated, and the firm is keen to ensure that its cybersecurity defences remain
In today's digital age, where data is the lifeblood of business operations, protecting sensitive financial information has never been more critical. The Payment Card Industry Data Security Standard (PCI DSS) was established to ensure the secure handling of card data, and compliance with this standard is mandatory for any organization that processes cardholder information. Achieving […]
In the ever-evolving world of IT, security has become a necessity more than a precautionary decision or a luxury that most organizations overlook. With the ever-increasing sophistication of cyberattacks, businesses are constantly seeking ways to safeguard their sensitive information and protect their customers' trust. Two widely recognized information security standards stand out in this
In today's dynamic business landscape, internal audit plays an even more critical role due to the complexities and the increased emphasis on
One of the key reasons for vulnerabilities in the applications are lack of secure design,
development, implementation, and operations.
Application Programming Interface or API serves as a data connection that facilitates the sharing of data with other applications. In today's rapidly evolving digital landscape,
Lok Sabha passed the Digital Personal Data Protection Act – India (DPDP Act) - August 2023 , India’s 2nd attempt in framing a privacy legislation.Aug 2017: Privacy as a fundamental right reaffirmed in Justice KS Puttaswamy vs Union of India by SC Justice Srikrishna Committee constituted to examine data
The Reserve Bank of India (RBI) has introduced a draft master direction that covers various domains of cyber resilience and digital payment security.
Passkeys are a significant improvement over passwords. They are faster, more secure, and more convenient. Many brands will follow in supporting passkeys. I expect passkeys to become the standard for login security in the near future like how 2FA was adopted in the past.
The cybersecurity landscape is constantly evolving, and CISOs need to be prepared to defend against increasingly sophisticated attacks.
Regulated Entities (Res) outsource a substantial portion of their IT activities to third parties, which exposes them to various risks. RBI released a finalized version of Master Direction on Outsourcing of Information Technology Services on April 10, 2023.
Portfolio managers work closely with their clients to understand their financial goals, risk tolerance, and investment preferences.
The GISEC 2023 event is scheduled to be held in Dubai World Trade Center, United Arab Emirates, on 14, 2023 to March 16, 2023.
The RBI announced the launch of the first pilot for retail digital Rupee (e₹-R) on December 01, 2022. It has commenced the pilot in the wholesale segment from November 2022.
An Account Aggregator shall transmit the financial data pertaining to the user only after receiving formal consent from the user
APIs are the backbone of the internet, powering the applications and services that we use every day
In order to protect your business from common cybersecurity threats, it is important to be aware of the different types of attacks that exist and how to prevent them
Read what RBI has to say on digital lending in the Guideline on Digital Lending issued on 2nd September 2022
The concept of BNPL is similar to that of credit cards wherein a consumer makes a purchase through a credit line and the payment is done later
Security Architecture Review is a holistic review of security that covers networks, Data, Applications, Endpoint, Cloud, etc.
Companies are realizing the benefits of cloud infrastructure. They are quicker to scale, cheaper to maintain, and more flexible.
Executive leaders of organizations and board members are ultimately responsible for ensuring the long-term security
With the year 2020 and the pandemic overwhelming us, we must be conscious of the increase in cyber security threats that are looming in front of us. Here are a few thoughts
Global situations relating to the COVID-19 pandemic have impacted the business and has also impacted the work of auditors. The current situations challenge the conventional
According to the statistics 73.2% of the most popular WordPress installations are vulnerable till date. These can be identified using automated tools and can be exploited.
Blockchain is an emerging technology that is quite popular nowadays due to the popularity of cryptocurrency. The blockchain contains a list of records or blocks which are linked using
Malvertisements are a malicious advertisement distributed in the same was as a legitimate online advertisement. It is one of the common practices to use spread malware.
CyRAACS is a great place to work because every day provides an opportunity to learn something new, to mentor and to be mentored to achieve our client’s goals.